All In One Course Creation, Delivery & Marketing Platform
Everything you need from Course Creation, Marketing Funnels, Email Automation to Community without needing to hire designers, developers or marketers.
GET STARTED FREENo Credit Card Required
Course Creation
Fully Featured Online Course Platform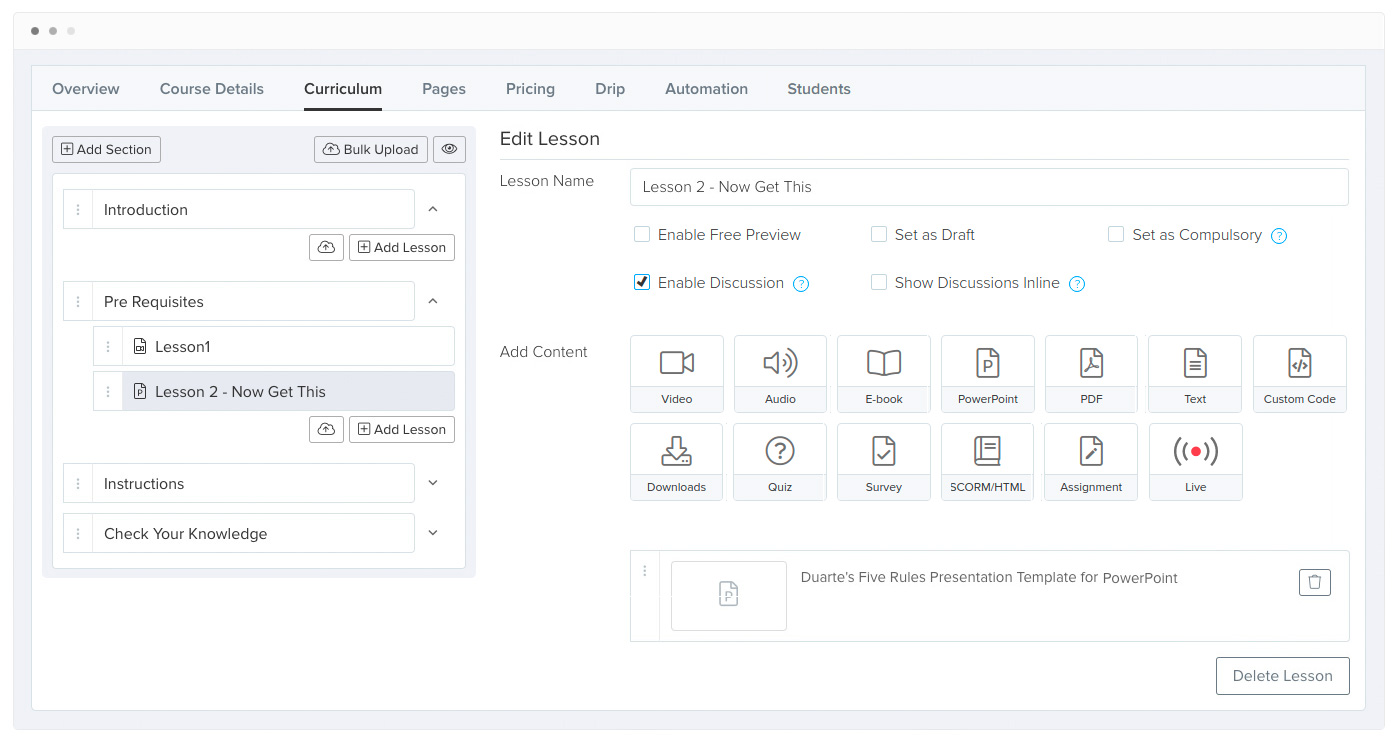
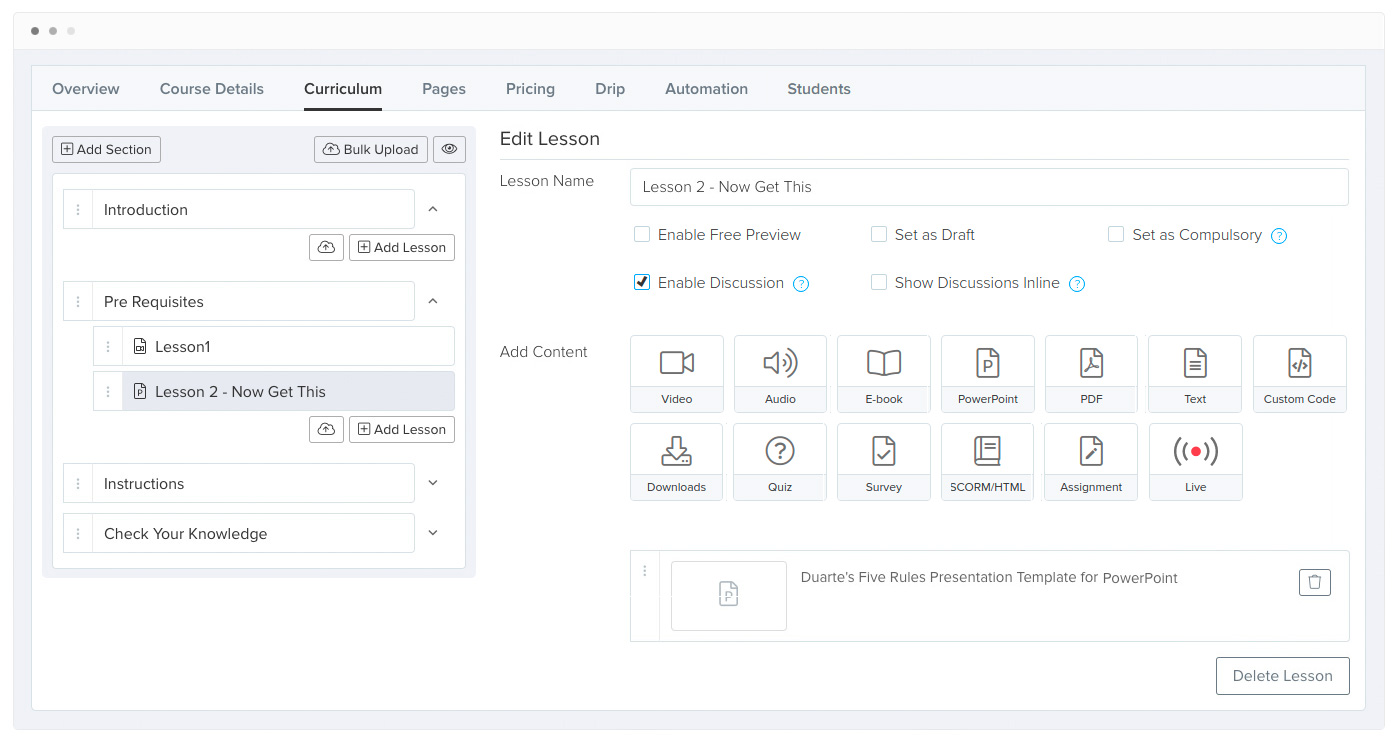
Easily Create Courses & Track Students
Add Videos, Audio, PDF, PPT, Quizzes, Surveys, Downloads & Live Videos(soon). Create Bundles & Membership Sites. Add Drip Schedules. Visualize your Course Funnel to improve conversions.
Set Any Pricing that you want
One Off Courses, Subscription, Free Trial, Payment Plans/Installment plans, Tiered Pricing Plans for splitting access level into your Courses/Bundles, One Click Upsells, Order Bumps(soon) & more.
Email Automation
Nurture your students with an entire sequence of emails based on triggers like Enrollment, Course Completion, Lesson Completion, Add Tags & Remove Tags. Pre-loaded High Converting Email Blueprints.
Marketing
Create any type of Marketing Funnel - Generate Leads & Build Your List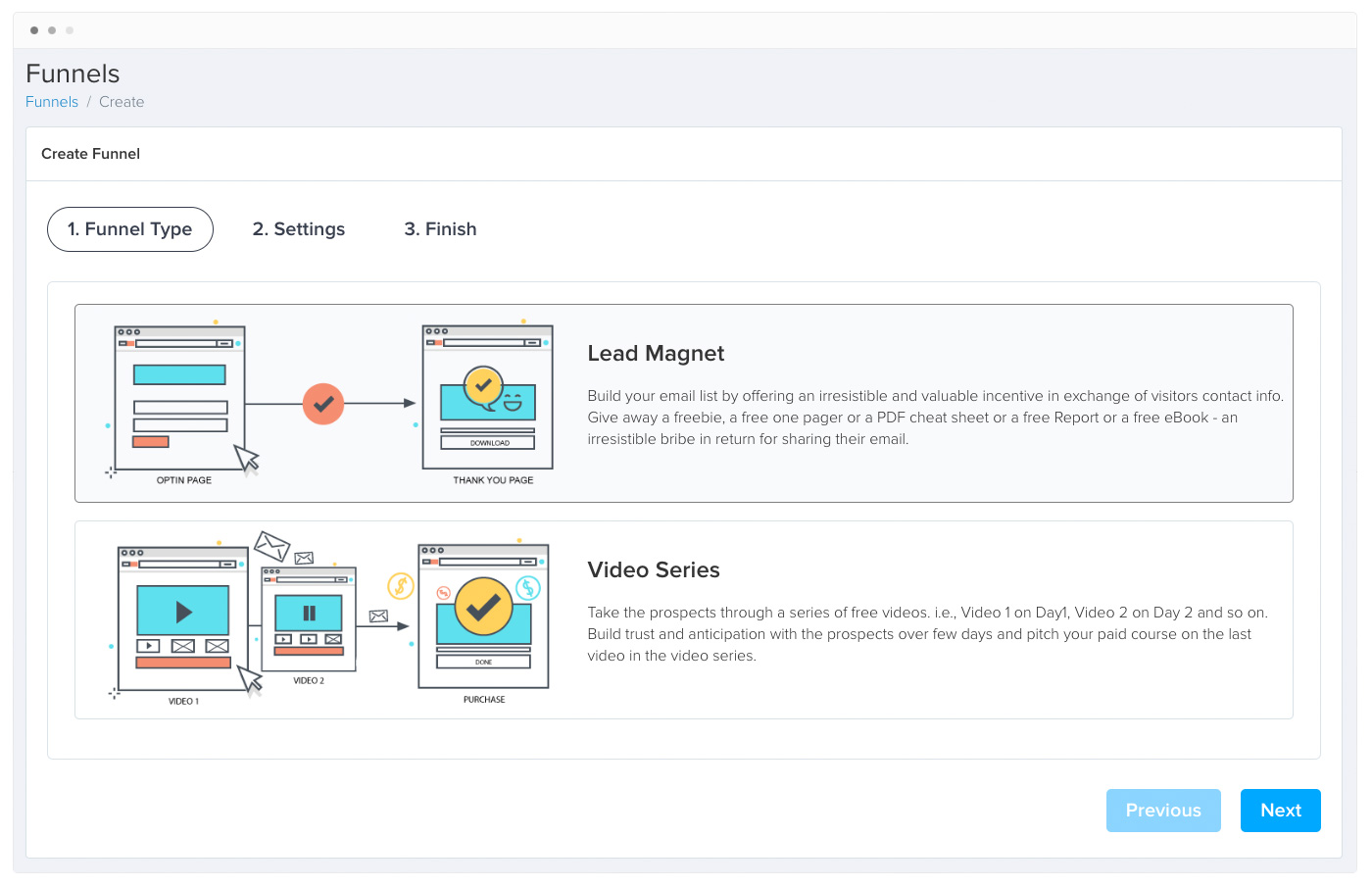
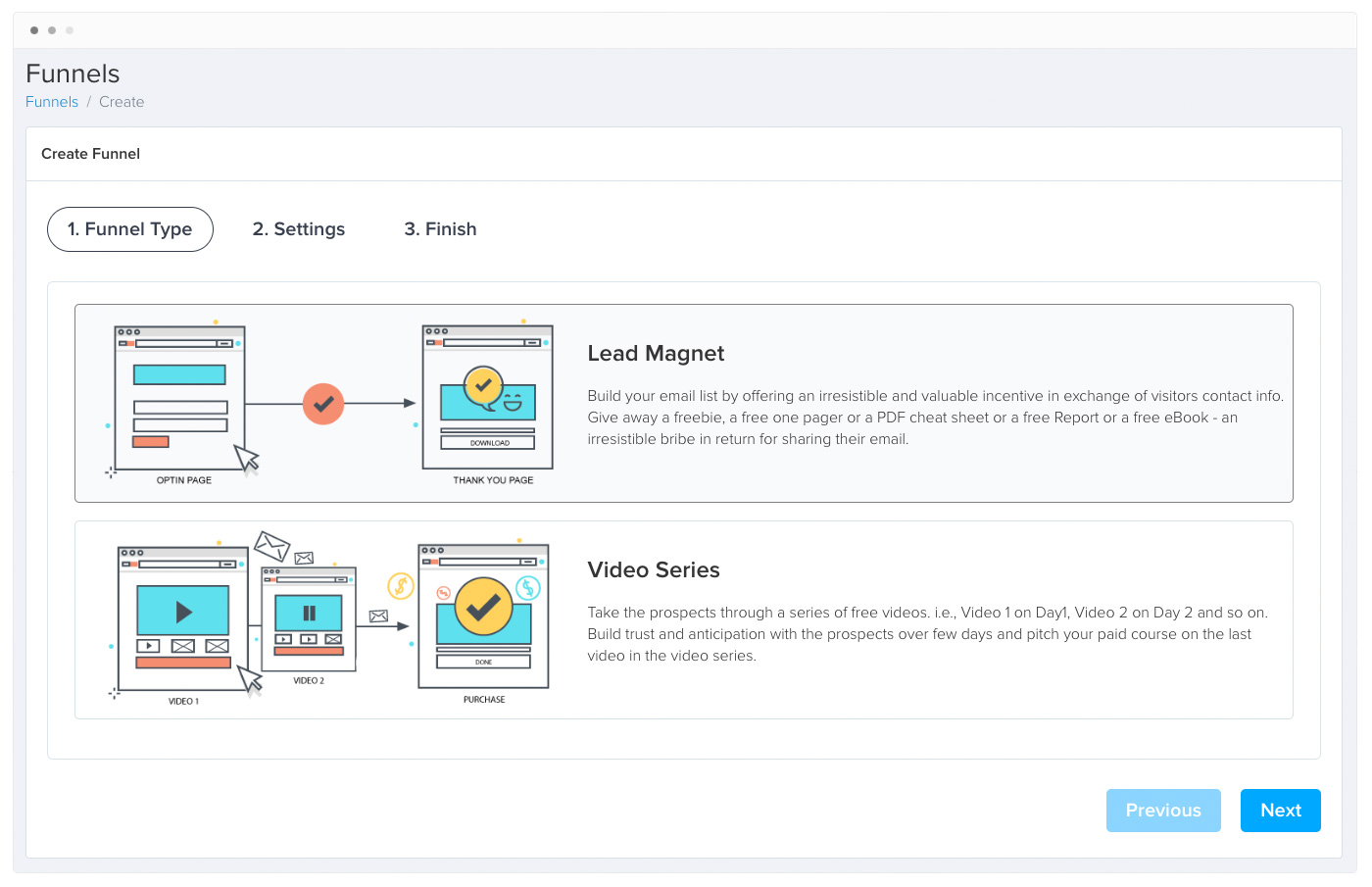
Easily Create Marketing Funnels
Create any type of High Converting Marketing Funnel - Lead Magnet Funnels, Video Series, Webinar/Automated Webinar/Survey/Virtual Summit Funnels(soon) & more in few clicks.
High Converting Designs
Choose from several high converting designs. Edit it the way you want in the powerful page editor. Visualize the funnel, see where visitors drop off, tweak & improve conversions.
Marketing Automation
Easily set up an entire sequence of emails or actions based on where the prospect is in your funnel. Segment and target them with messaging the way you want. Pre-loaded Email sequences.
Email Automation
Easily setup Automated Emails and other Actions based on events & triggers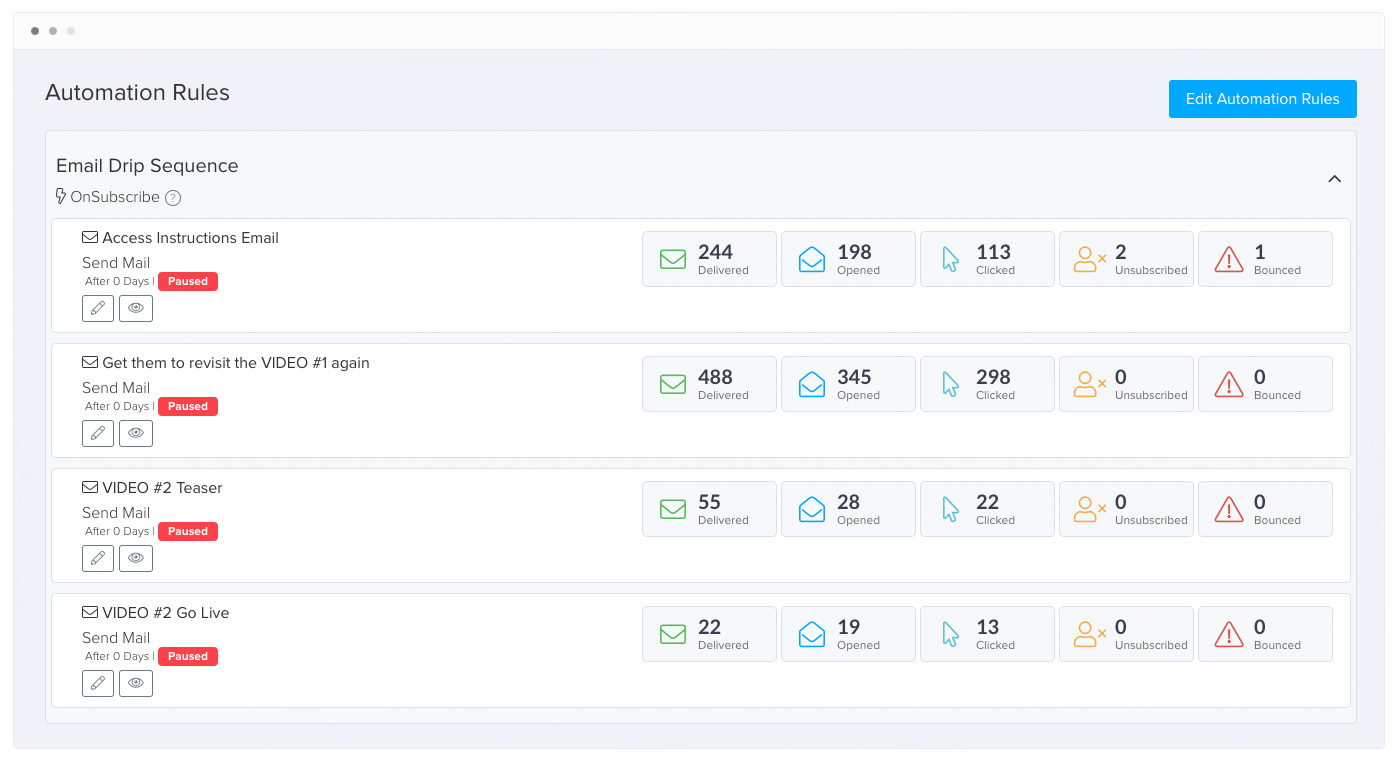
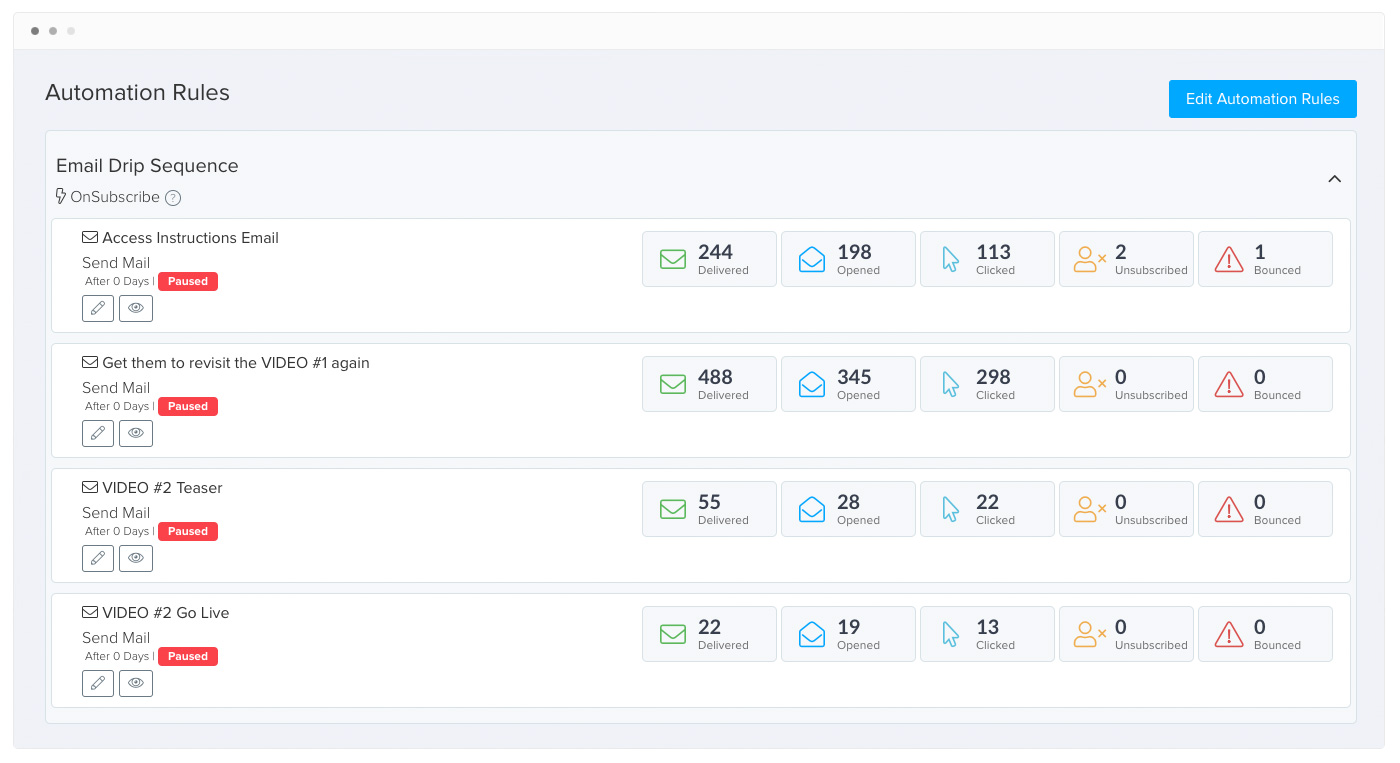
Zenler Mail - Built-in Email System
Send and Schedule Emails from right within Zenler without needing any third party email/email automation service. Seen clear cut stats of mail opens, clicks, unsubscribes right inside your site.
Email Automation
Send emails automatically when someone signs up to your course or funnel, completes a course or a lesson etc. Drip delay your emails. Automate Tagging & more
Powerful Segmentation
Send emails that target the right people at the right time. Segment your contacts based on easy to use filters. Use segmentation when sending emails inside your course, funnel or in Email Broadcasts.
Page Designer
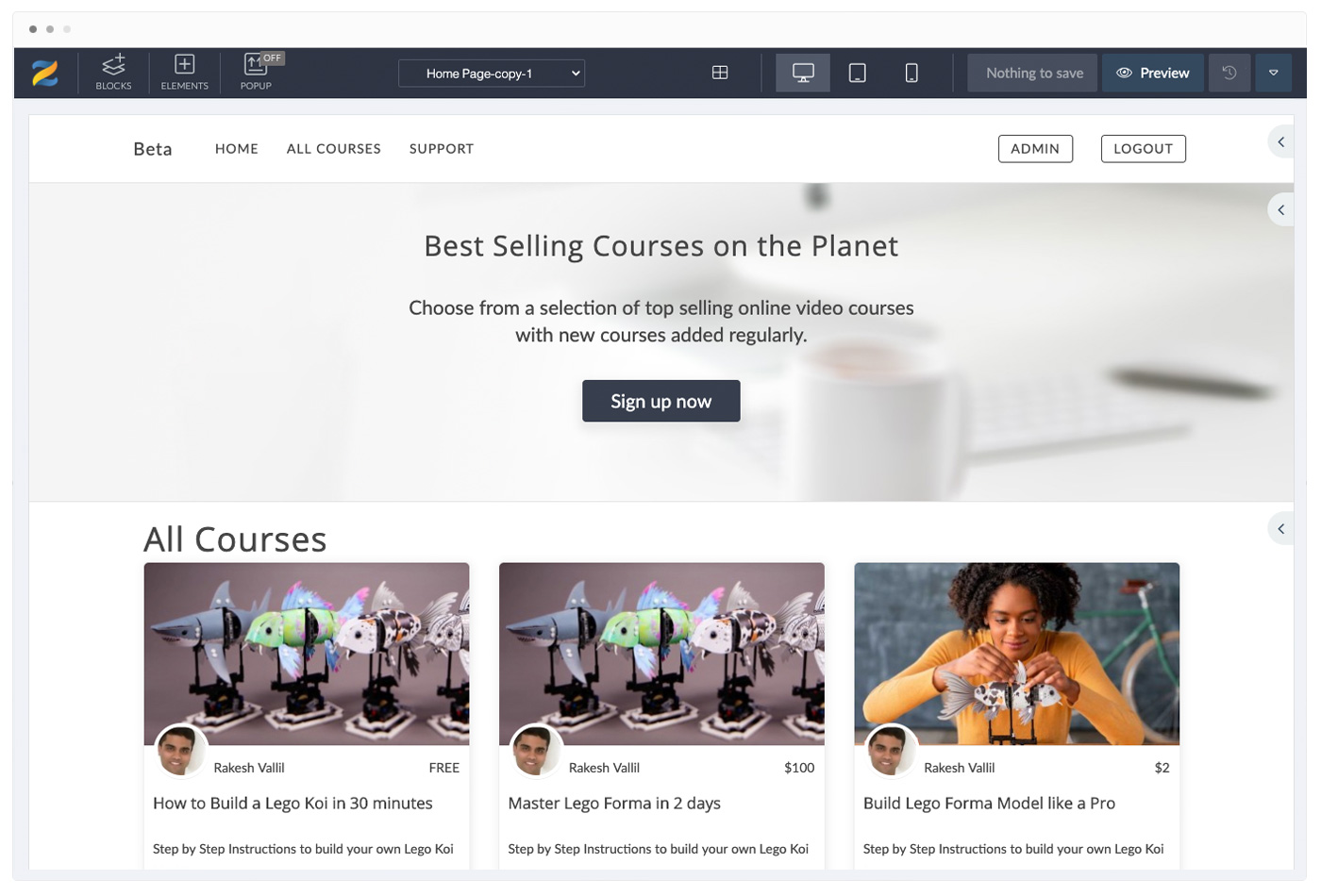
Drag & Drop Page Designer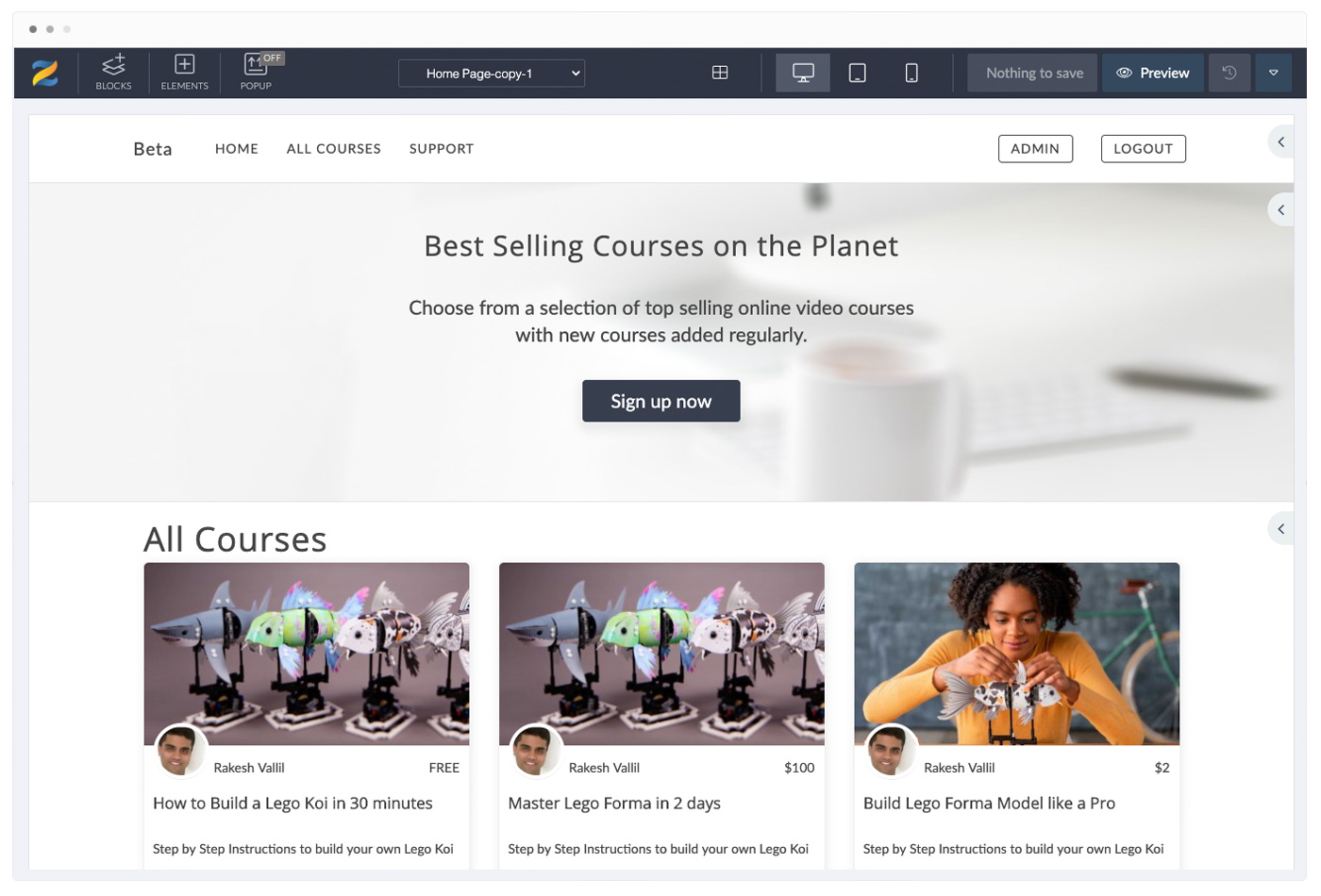
Create any Page Design that you want
Customize any of your pages to your heart's content like never before! You are not stuck with a few hardcoded designs to choose from. Easily add, edit, drag and move any elements on the pages.
All without any Coding / Web design expertise
1000+ premium ready to click and edit design Blocks for you to quickly create high converting landing pages. Drag and drop any Elements you want into your page - text blocks, pricing tables, buttons, images, videos & even countdown timers.
Easily Design Popups
Choose from a collection of premium done-for0you popup designs. From being able to display popups when someone tries to exit your page to displaying popups after a delay you are in total control.
Community
Drive Student Engagement With Community & Live Chat Room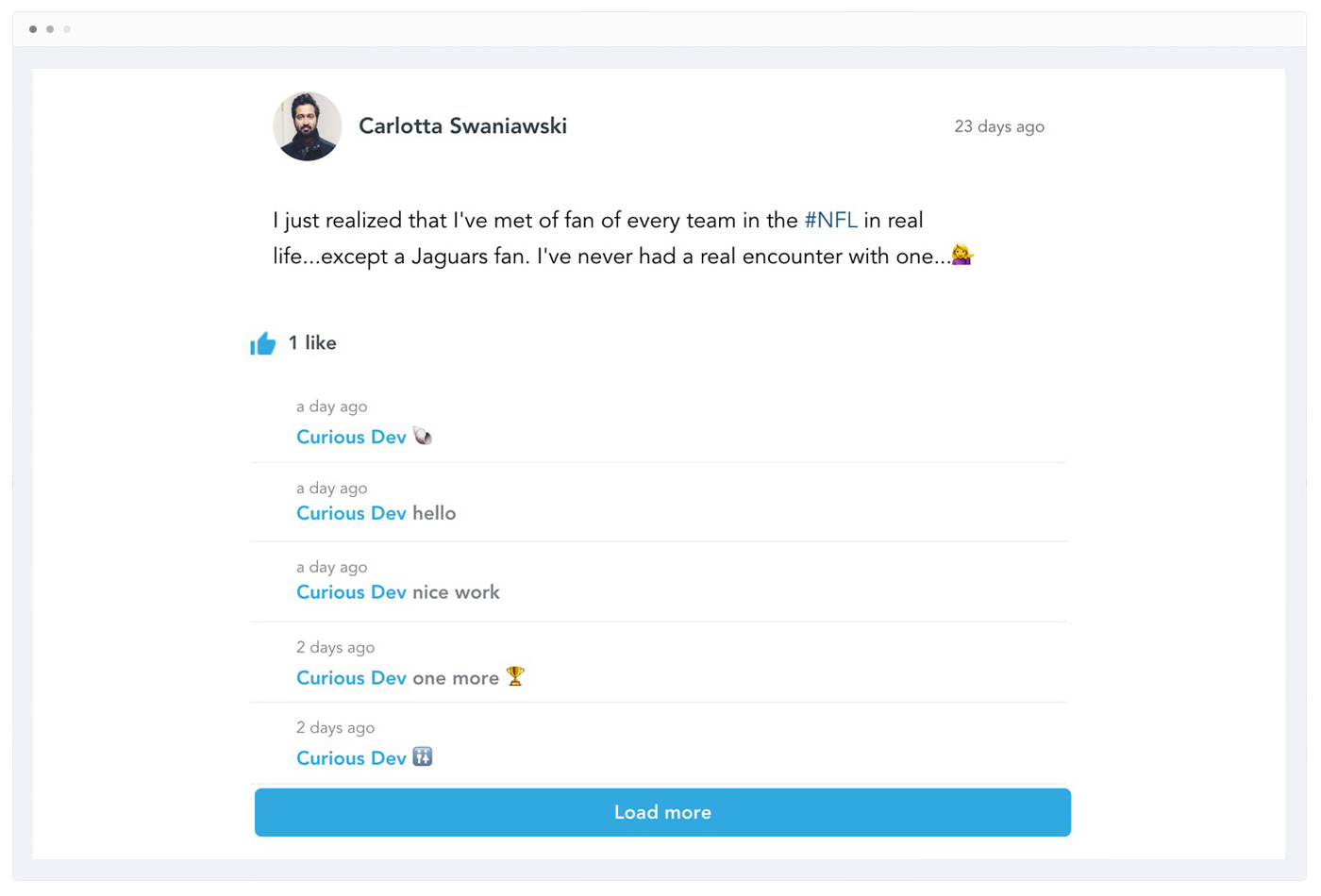
Community
Easily setup a social network-style Community for your site. Community baked into your site can help trigger network effects to form a strong community for your courses and membership sites.
Live Chat Room
Live Chat Room supplements community to have a live chat area where members can communicate in real-time driving even further engagement.
Add Community & Live Chat to Pricing Plans
You can decide who gets to see the community and live chat. You have the option to include Community and/or Live Chat on the pricing plans.
Live Classes, Live Webinars, Live Interactive Webinars & Live Stream
Create and Run Live Classes, Live Webinars, Live Interactive Webinars & Stream Live all in HD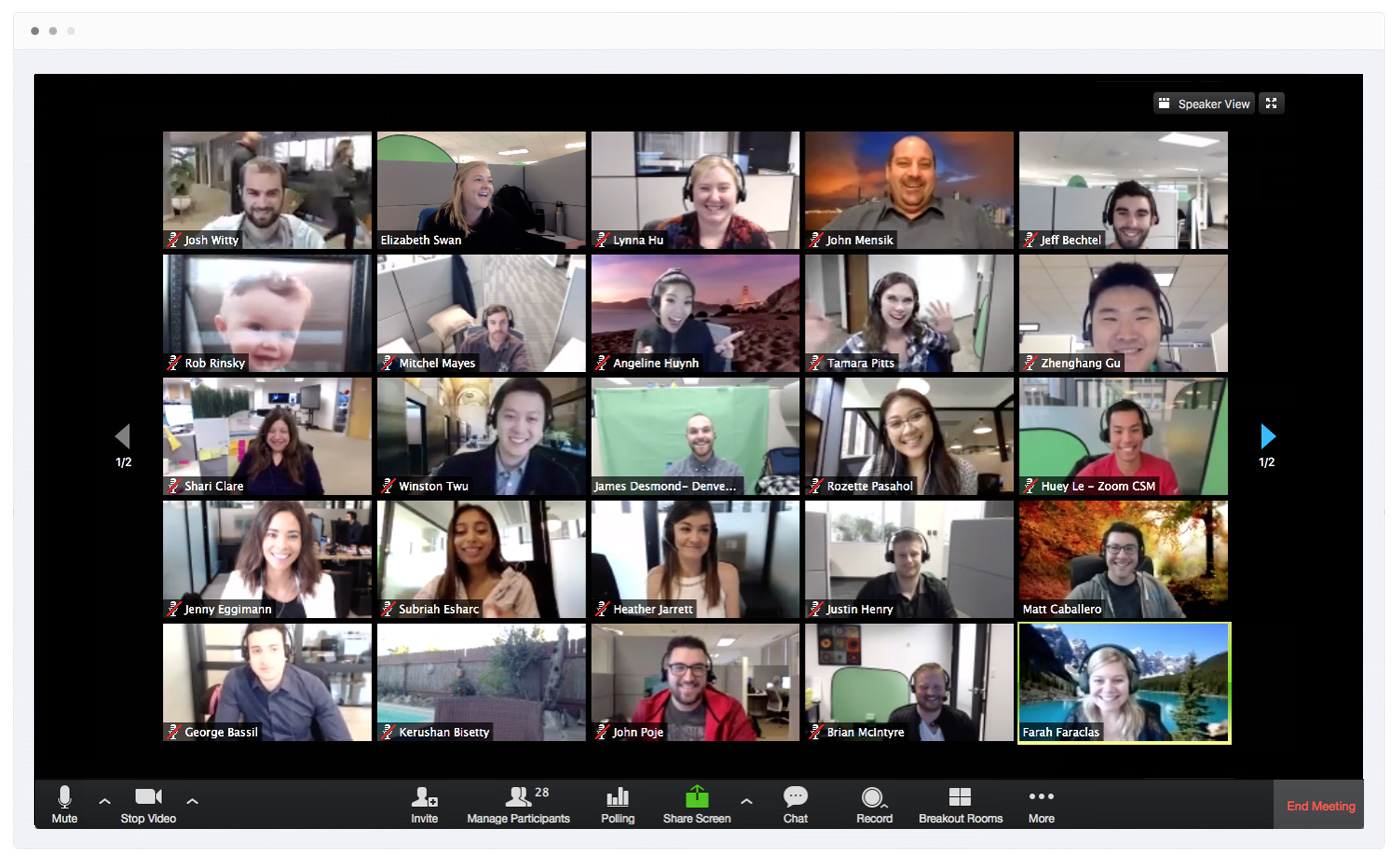
Schedule & Run Live Classes
Run Live Classes for your students with HD Video and Audio. Up to 500 video participants and 49 videos. Built-in Chat, Screensharing, Security, WhiteBoard, Recording, Virtual Backgrounds, Share Files, Breakout Rooms & more.
Run Live Webinars
Setup and Run Live Interactive Webinars with HD Video & Audio. Up to 500 attendees. Chat, Screenshare, WhiteBoard, Security, Share Files & more.
Live Stream your session to Facebook Live or Youtube Live
Broadcast Live Streams into your Facebook Live or Youtube Live - build and engage with your audience and prospects.
 Course Creation
Course Creation
 Marketing
Marketing
 Email Automation
Email Automation
 Page Designer
Page Designer
 Community
Community
 Live
Live